UltraWAF - Web Application Firewall
HTTP: http://www.vercara-se.com | WAF: http://waf.vercara-se.com
Violation Logs
Violation Input Value =
Violation Reason =
POST Body Limit
Negative case for POST Body Limit. Should be allowed. Request body is <500 bytes.
Positive case for POST Body Limit. Should be blocked. Request body is >500 bytes.
HTML SQL Injection
Negative case for SQL Injection. This should not be flagged as SQL Injection because of grammar checking even though it has a lot of SQL reserved words that are also in common English if you own a furniture store.
Join to steal credit card data.
Login bypass.
The Bobby Tables Attack. [ref]
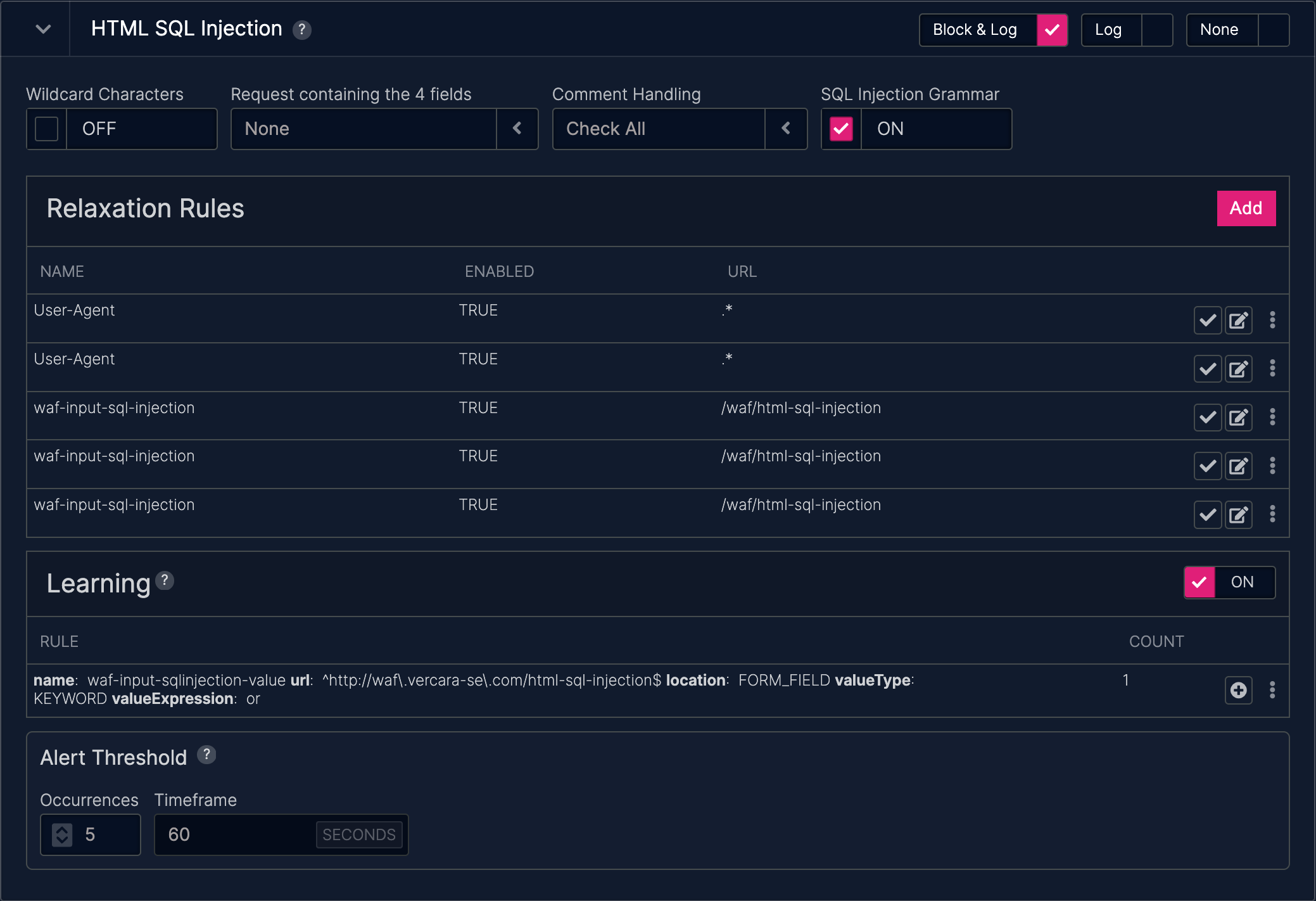
SQL Injection
A SQL injection attack consists of insertion or "injection" of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system. SQL injection attacks are a type of injection attack, in which SQL commands are injected into data-plane input in order to effect the execution of predefined SQL commands.
Buffer Overflow
Max length for URL = 100 bytes
Send 121 byte URL string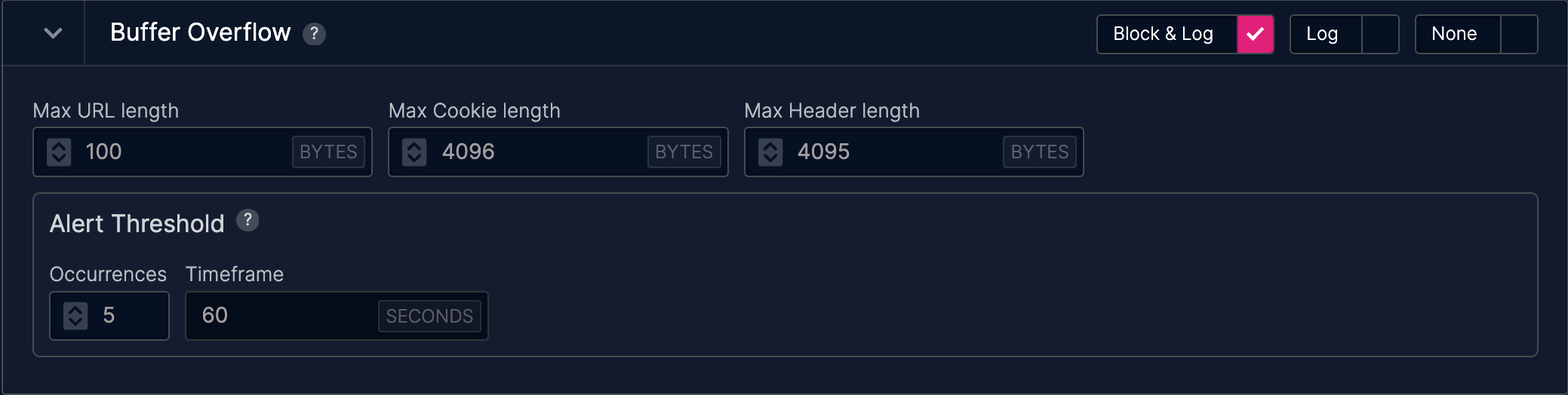
Buffer overflow attack
Buffer overflow errors are characterized by the overwriting of memory fragments of the process, which should have never been modified intentionally or unintentionally. Overwriting values of the IP (Instruction Pointer), BP (Base Pointer) and other registers causes exceptions, segmentation faults, and other errors to occur. Usually these errors end execution of the application in an unexpected way. Buffer overflow errors occur when we operate on buffers of char type.